Insecure Transit - Microservice Security
60min Presentation
A deep dive into some of the technical challenges and solutions to securing a microservice architecture.
Microservices are great, and they offer us lots of options for how we can build, scale and evolve our applications. On the face of it, they should also help us create much more secure applications - the ability to protect in depth is a key part of protecting systems, and microservices make this much easier. On the other hand, information that used to flow within single processes, now flows over our networks, giving us a real headache. How do we make sure our shiny new microservices architectures aren’t less secure than their monolithic predecessors?
Picking up where my previous presentation on this topic left off, in this talk, I outline some of the key challenges associated with microservice architectures with respect to security, and then looks at approaches to address these issues. From secret stores, time-limited credentials and better backups, to confused deputy problems, JWT tokens and service meshes, this talk looks at the state of the art for building secure microservice architectures.
Key topics
I cover a number of topics in the context of microservices, including:
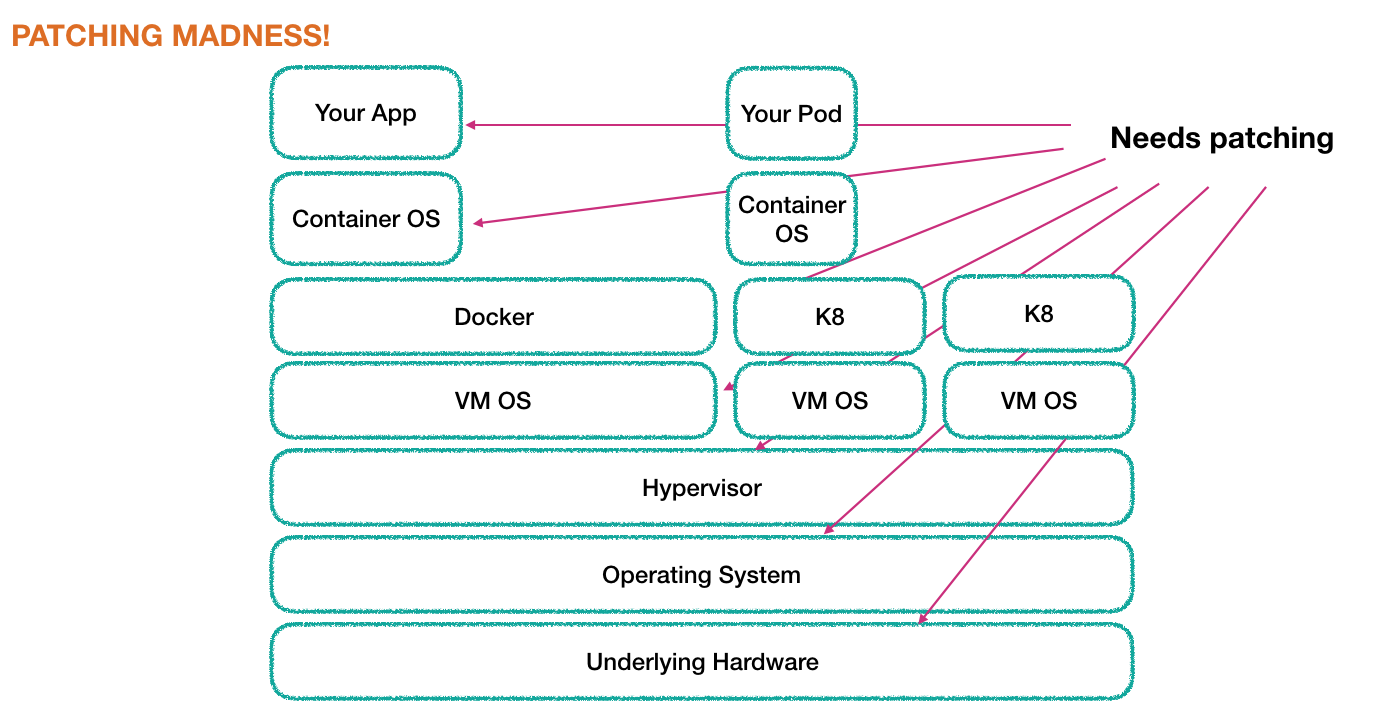
- Basic password hygiene
- Patching pain!
- Secret storage
- Securing transport
- Authentication and authentication - including use of JWT
- Role of service meshes
Audience
Anyone who is currently building, or planning to build a microservice architecture. I used to say "anyone who cares about security of a microservice architecture" but I sort of feel that if you are building software of any sort and don't care about security, then something is wrong! I don't expect people to be experts in security to understand what I am sharing, I focus on helping developers get "just enough security" knowledge to be useful.
Key Takeaways
- Microservices can make implementing secure systems easier and harder
- You have to think about security concerns up front
- There are some technology solutions that can make this less daunting and easier to consider
- That any developer building a distributed system can and should have some level of awareness of security issues, and be able to do something meaningful about them
Video
You can see a recording of this presentation from QCon London over at InfoQ.
Material
You can view the slides here, although please note that given the way I use presentations, it may be hard to get a sense of what the talk is about just by looking at the slides.
